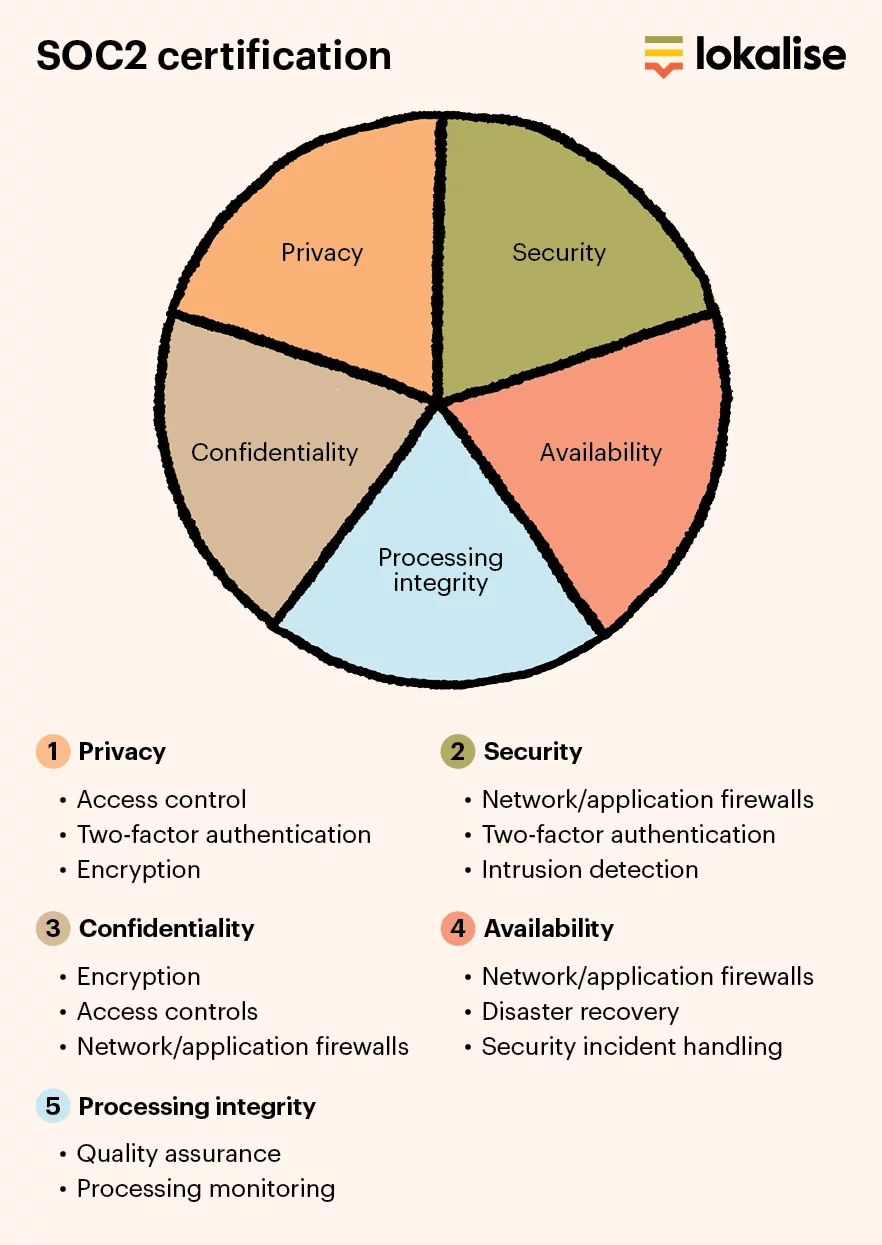
We are happy to announce that Lokalise has been certified according to ISO/IEC 27001 and ISO/IEC 27017 standards as of November 2020. As this milestone has been achieved, it is time to step back and look at the broader picture.
Today, we’re taking a closer look at what “good security” actually is and how it relates to Lokalise as a platform, service, and a company in general.
About product and data security
When people ask about how secure your product is, what is the first thing that comes to your mind? Is it about secure data – that no one without permission can access it? Is it about availability – that the service is always running and never goes down?
Or maybe it is all about keeping hackers away – preventing them from stealing data or affecting the system?
The more we think about this simple question, the more complicated it gets. And if we start digging into technical details, then it becomes as clear as mud.
Let’s look at this from a different perspective and ask the following question: What should a company do to ensure I can trust them with my data? This is the big revelation: TRUST is what matters the most.
Information security is important, but it is not the only factor that plays a role here. If I do not know the person or the company I want to work with, how can I trust them?
There are multiple theories around trust and how it’s built, but for the sake of this post we can say that common values or beliefs are a good starting point. Also, predictability is key:
Trust means being able to predict what other people will do and what situations will occur. If we can surround ourselves with people we trust, then we can create a safe present and an even better future
This applies to B2B relationships as well, where one company wants to understand and predict what the other company is (or will be doing) with its data. This is the point where industry-wide, accepted certifications come into play.
The ISO 27001 certification, explained in simple terms
Standards such as ISO/IEC 27001 and its relations lay a common ground for understanding each other, even when we have not met previously. It is the same as having a driver’s license – if you have one, we can safely assume that you know how to drive and follow general traffic rules, so we can happily hop into your car.
Lokalise has maintained SOC 2 Type 2 certification for more than a year already. Now, by adding IEC/ISO 27001 and its extension, IEC/ISO 27017, we can say that we have all the necessary driver’s licenses to operate and secure our system and customer data.
Now let’s look at the practical similarities and differences between the IEC/ISO 27001 and SOC 2 Type 2 certifications.
As a side note – we have to bear in mind that these certifications are governed by different organizations (ISO and AICPA, respectively) and that SOC 2 is more recognized in North America while ISO 27001 is widely known in the rest of the world.
In terms of practical everyday security, both standards cover everything starting at the governance and risk management level, and then going down to very practical aspects like physical security, access control, incident management, and others. Some say that the difference is in 5-15% of the controls, but it also significantly depends on the implementation side of things.
When we started our security program, we already knew that one day we would hold both certifications. So, right from the very beginning the policies and processes were designed with respect to both standards.
This way, only minor adjustments were necessary to fit our information security management system (ISMS) which had already been examined twice according to SOC 2 to the ISO 27001 requirements.
One of the biggest differences between these two standards lies in the way the examinations themselves are carried out in terms of their scope:
|
SOC 2 Type 2 |
The audit looks at actual evidence of completed controls from the previous period (in our case, this was 1 year), much like in a financial audit.
Some of the elements that are examined include the way user accounts are created, whether or not all service tickets are available, how changes into production systems are introduced, if sufficient testing has been done, etc. Every year we have to do a complete SOC 2 Type 2 examination from scratch. |
|
ISO 27001 |
With ISO 27001, we are certifying the entire information security management system (ISMS). This proves that we have a company-wide, ongoing operational, risk-based, and managed security system in place, and that it’s running smoothly. |
There is a 3 year certification cycle for ISO 27001 with the full audit in the first year and smaller recertification audits in the second and the third years.
The certification audit is different from SOC 2, with the main focus being on continuous improvement, risk management, and running a successful ISMS as a whole.
Nevertheless, it can get down to the same technical details as the SOC 2 audit.
The ISO/IEC 27017 (Information technology—Security techniques—Code of practice for information security controls based on ISO/IEC 27002 for cloud services) is an extension to the ISO 27001 standard, which provides guidance for the security of cloud service providers in more detail than ISO27001/2.
With this certificate, topics like the shared responsibility model, relationships between the cloud service provider and its customer, or use of shared resources, are all covered.
In a nutshell, we have been using these guidelines to align and adjust our internal processes and procedures to ensure we meet the highest standards and comply with industry best practices.
Summary
To summarize all of the above – we have done (and are doing) a lot to remain a reliable and trusted partner to our customers, in terms of security and data protection. Of course, that doesn’t mean that we are stopping here. There is a lot to be done and with the ever-changing security environment around us, we will do our best to continue improving.
This was the first, high-level introduction to Lokalise security. You can expect more detailed (and also technical) posts in the near future. In the meantime, you can learn more about Lokalise security measures on our website.